At Cisco Live EUROPE 2019 Victor Moreno and Mike Herbert presented Cisco´s Application End to End Policy strategy. Often Policy enforment is just a check box features that is added to a product. To integrate the capability for one product to enforce polcies based on some kind of TAG is the easy part. Much harder it is to integrate that across multiple platforms and products. I appreciate that Cisco is making huge efforts to develop a consistant policy strategy across their portfolio to make it a solution and not just another feature.
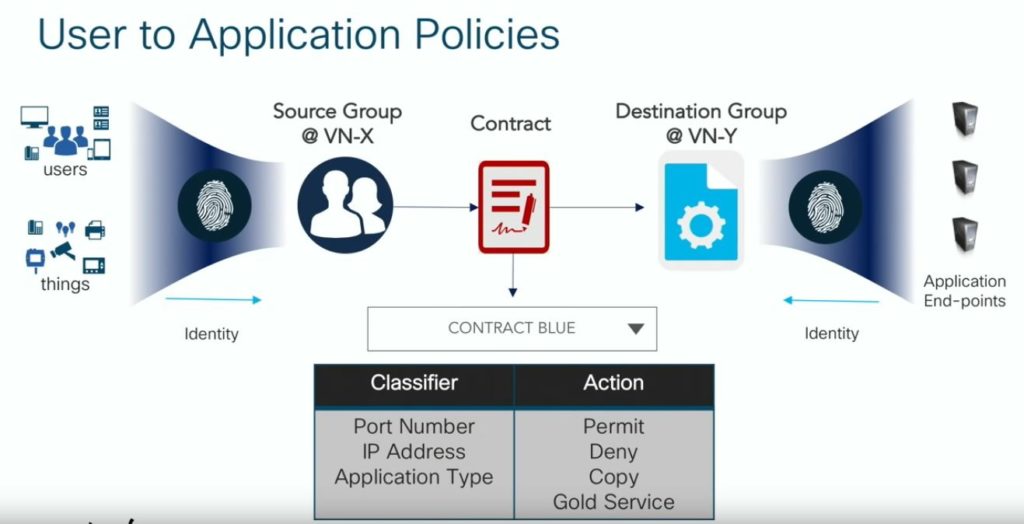
To make it end to end the second chellange is to keep the policy frame work User based. IP based access list are not flexible enough to meet the modern dynamic enviromonts. That was the reason why a lot of previous approaches have been failed to address the end to end scenario. Here the User Identity is capture on the Login and the corosponding policies for that particular User will applied to the Infrastructure danamically.
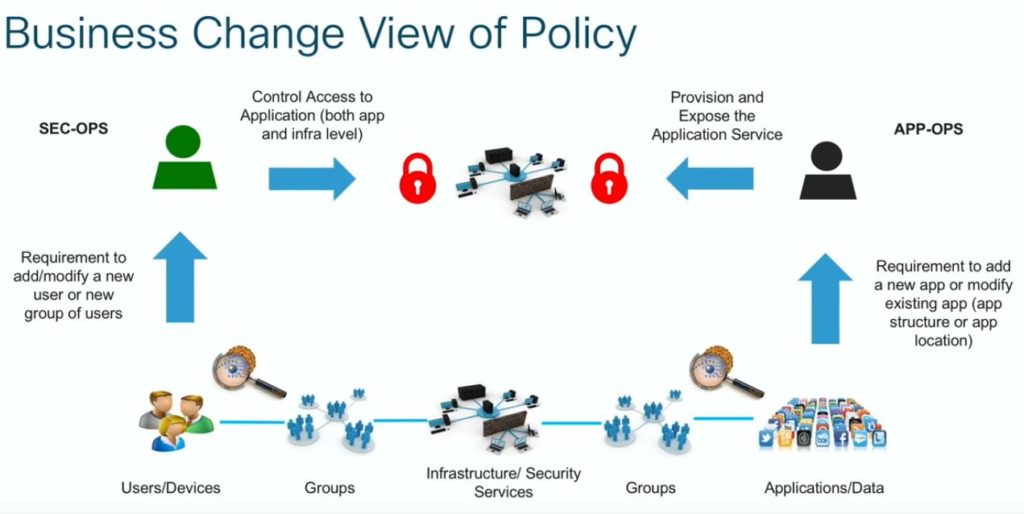
Cisco is using the 16bit Header that was also used for the Secure Group Tag (SGT). In this case the same field is embedded into VXLAN where it is called Class ID. The benefit in that implementation is that this is not bound to L2 and can be carried across L3.
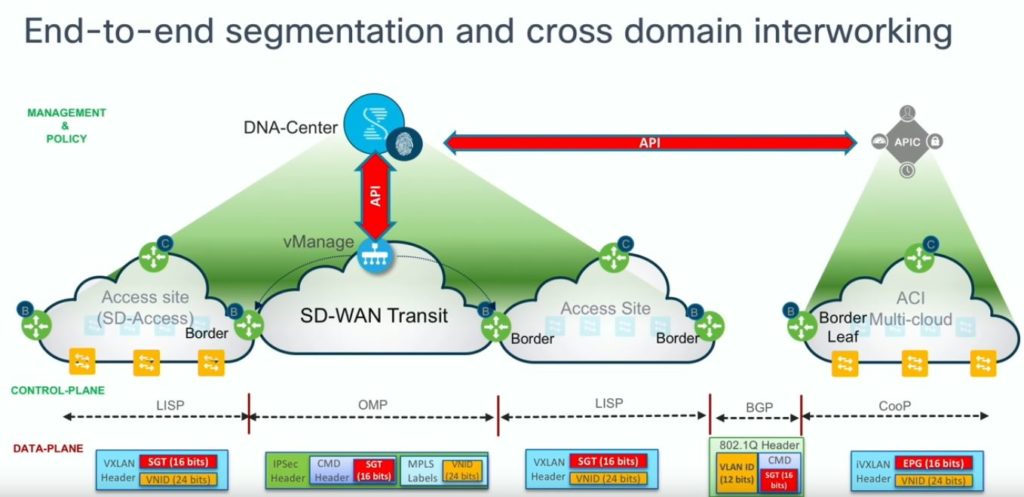
To keep the Tags consitant across multiple Controller domains a sync needs to happen between the different controllers. In this scenrio ACI APIC and Vipetella SDWAN vManage Controller are both synconized via API with the DNA Center. That decentrelized approach looks scalable enough and does not need an “Uber Master Conroller”.
Network Autobahn View
Good that Cisco is making this effort to bring a solution that is really solving end to end problems. Manually Security TAG Translation is not scalebale nor manageable. For me this is going in the right direction and looks like a solution that is usable in real world scenrios. Looking forward to see this and the Firepower integration in action.




