 Cisco has introduced at the Cisco Live the new FirePOWER 4100 device Family. besides a new Hardware Platform the really interesting development is going on the backround. First a short brief of the new 4100 appliances, they come out in 3 different versions at the start and a 4th model will be added in the 2nd half of 2016. It is a 1RU appliance that can do up to 20GB/s FW throughput with L7FW, AVC and IPS enabled.4100 NGFW Datasheet
Cisco has introduced at the Cisco Live the new FirePOWER 4100 device Family. besides a new Hardware Platform the really interesting development is going on the backround. First a short brief of the new 4100 appliances, they come out in 3 different versions at the start and a 4th model will be added in the 2nd half of 2016. It is a 1RU appliance that can do up to 20GB/s FW throughput with L7FW, AVC and IPS enabled.4100 NGFW Datasheet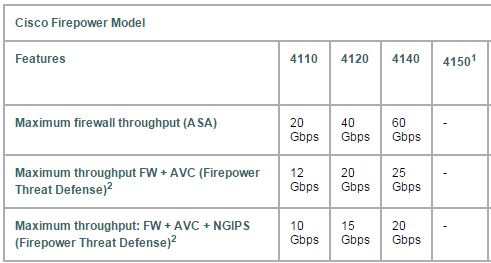
The real interesting point here is that you can run the unified image for that. In the past we had an Hardware box that runs the ASA code and on top of that the FirePower as an additional instance. I always simplified that in my mind like an VM that runs on a server and in this VM the Firepower was living. To scale that model up you needed additional processing power. For example in the 5585-X models you had 2 devices inside of one chassis. On one part the ASA code was running and on the other the FirePower. That means from a packet flow prospective the packet was proceeded and inspected two times, first from the ASA based code/HW and when that was finished it was passed to the FirePOWER engine to get inspected and processed again. That changes now now with unified Image approach. The functions and features of the ASA have been ported to the FirePower code so that there is no need two run 2 images any more. Finally we have a integration of the L4 statefull inspection and L7 content based polices. At the moment there are missing some of the VPN features, hopefully we will see these functions added in one of the future releases.
To leverage the new unified FirePower 6.x Image approach there is also an Management solution available. Instead of dealing with Cisco Security manager or prime Security manager for the State full inspection L4 rules and the FireSIGHT manager for the L7 content aware policies this is also unified in the “Cisco Firepower Management Center” . It looks very much like the previous FireSIGHT interface and has some additional functions. I like that you now see all polices in one place regardless of the type of policy. FirePOWER Threat Defence for ISR and Advanced Malware protection (AMP) can be managed from here as well.
The Network Autobahn View
It was a long way but finally Cisco has integrated the FirePower NGFW and IDS/IPS Service based on SNORT with a state full inspection FW. That tight integration and a central policy choke point make a lot of sense. This combined with the centralized Management and Logging makes together a great solution. In the past the handling with ASA “ACL” based rules and NGFW L7 content based policys was always difficult to handle. I got the impression at Cisco Live that the new combined Image is the future and the old ASA will fade away completely in the future. A state full Inspection FW is pretty much the security modell of the late 90s and I think even the term “Next Generation Firewall” is outdated. Deep Packet inspection has become the only way to do security and Port numbers are pretty much irrelevant. I am looking forward to the next FirePower Releases that hopefully brings also the VPN features to the unified Image.





As you mentioned packets had to be processed by two different engines but this has in fact not changed. The “unified” image is firepower linux with asa running as a process on the system. Traffic is redirected into the asa process and is then processed by firepower. So now we basically got it the other way around.
Hi Oliver,
year you are correct on that. The ASA code is living on a container that runs on the Firepower FTD OS. Maybe it would have been more optimal to rewrite the code and implemented the L4 statefull inspection features nativly on the FTD OS , but that would have been the bigger task from the development standpoint. On the Firepower 4k series it runs nativly the FXOS witch Cisco calls a eXtensible Operating System. or from my point of view a hypervisor. The FTD image runs like a VM on the FXOS. witch ends up with all the benefits and penaltys that a VM based system has.
Cheers
Dominik