At Cisco Live Jonny Noble presented a session at the Tech Field Day Extra Event.
It was covereing the Umbreall and AMP for Endpoints from Ciscos Security group.

I will focus here on the updates of AMP for Endpoints and what has changed in
the product. AMP for Endpoints has been around for quite some time and was in the
past mainly focussed on File Protection and EDR usecases.Cisco has put a lot of development into the product and is fast moving forward with it.
From a more nish targeted product it has now grown to a fully featured Endpoint protection solution that is now also covering classic Anti Virus endpoint protection. Besides that Cisco has One-to-one signature, fuzzy fingerprinting , Machine Learning, rootkit scanning and Sandboxing capabilities built into AMP for Endpoints.
The management componenet is mainly deployed as a cloud solution. Cisco is also offering an on prem variant for those customers that do not want to go to the cloud.
On the OS side they support Windows, MAC OS, Linux (RHEL/CENTOS) and Android nativly.
Cisco now added an intergration for Apples IOS based IPhone devices with a new Client called Clarity. Will take a deeper look what is possible with this client and how deep the client is intergerated into Apples mobile device OS.
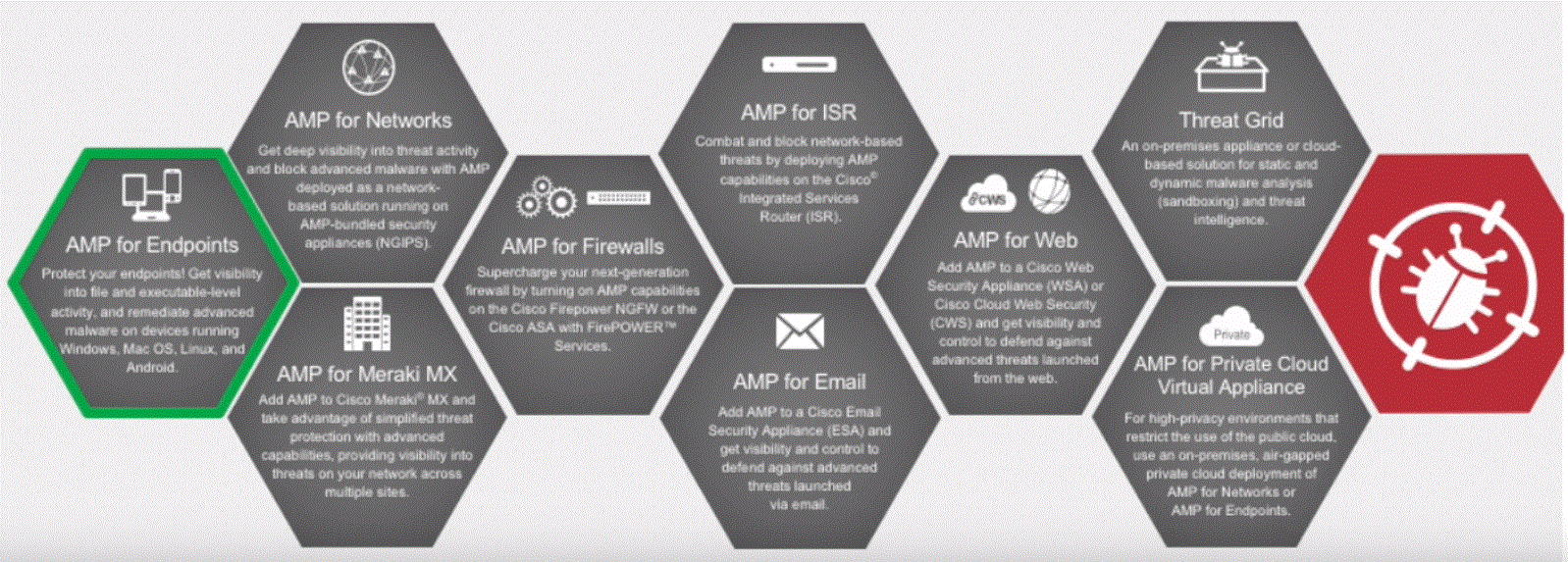
There are a lot of Endpoint Protection / AV products on the market, what is unique to Cisco AMP for Endpoints is the integration with the other AMP solutions.
This integration is from my point of view one of the key differentiators. Cisco has also integrated AMP for Meraki MX, Firepower, WSA, ESA and Threat Grid.
A good example is a retroperspective event and how you can investigate these. In case
a file was downloaded to a Client PC in a corporate network, it can pass multiple devices that are running AMP like the Web proxy / WSA or Firepower based NGFW. Maybe at the first day AMP was not able to detect that this file was malicious. In the moment the automated Threat feeds have been updated it can detect this malicious file. In the mangement console it will mark based on the logs the hash of this file and present it as a retroperspective event. Now you are able to detect where this File has been shown up in your enviroment. After AMP is aware that this file is malicoius it will start blocking the file. It is now easy to pin point where the file has been showing up in your infrastructure with the file trajectory and to track the potentially latural movement of it.
For more details check out the recorded Session:
Cisco Cloud Protect: A Quick Dive Into Cisco Cloud Security with Jonny Noble
Please accept YouTube cookies to play this video. By accepting you will be accessing content from YouTube, a service provided by an external third party.
If you accept this notice, your choice will be saved and the page will refresh.




