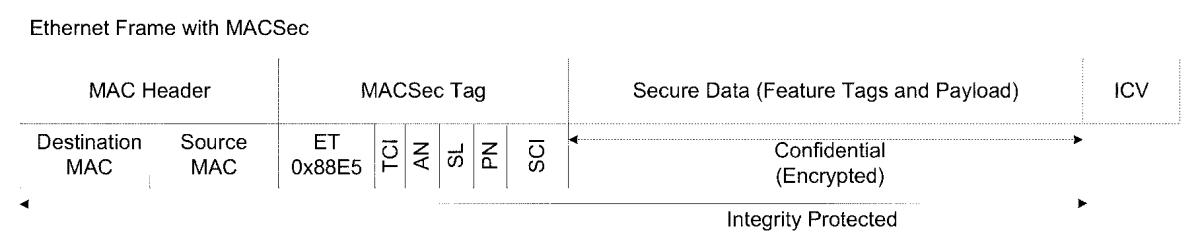
 The IEEE 802.1AE MAC Security standard or also known as MACsec discribes a point to point encryption for Interfaces. The encryption uses an AES cypher. I like the idea that you can encrypt all the uplinks in your network with a basic protection that adds nearly no latency and works on full line rate. To get encryption for 10 Gigabit connections with traditional VPN appliances is very expansive and adds a fair amaount of extra latency. The encryption proccess for MACsec is done from the hardware asic that gives the benefit that it is very fast without the need of extra cpu time. You can do the encryption direct on Layer 2 wich makes it transparent for your network. At the moment MACsec gets available on more platforms across many vendors so that is possible to build a network with only MACsec capable hardware with planty of choices. For example Avaya has MACsec capable hardware in the VSP4450GSX, VSP8200, VSP7200, ERS5900 and the VSP9k 9048XS-2 line cards. MACsec is only supported on the SFP+ Ports on these devices. I show step by step what is needed to enable MACsec on a VSP switch.
The IEEE 802.1AE MAC Security standard or also known as MACsec discribes a point to point encryption for Interfaces. The encryption uses an AES cypher. I like the idea that you can encrypt all the uplinks in your network with a basic protection that adds nearly no latency and works on full line rate. To get encryption for 10 Gigabit connections with traditional VPN appliances is very expansive and adds a fair amaount of extra latency. The encryption proccess for MACsec is done from the hardware asic that gives the benefit that it is very fast without the need of extra cpu time. You can do the encryption direct on Layer 2 wich makes it transparent for your network. At the moment MACsec gets available on more platforms across many vendors so that is possible to build a network with only MACsec capable hardware with planty of choices. For example Avaya has MACsec capable hardware in the VSP4450GSX, VSP8200, VSP7200, ERS5900 and the VSP9k 9048XS-2 line cards. MACsec is only supported on the SFP+ Ports on these devices. I show step by step what is needed to enable MACsec on a VSP switch.
To configure MACsec on the VSP you need first to create a cennectivity association wich is assosiated with a key. This is not shown in the running config for security reasons. The ca-name can be up to 32 Byte alphanumeric signs and the key cak-value up to 80 Byte alphanumeric signs.
macsec connectivity-association test connectivity-association key (cak-value)
When you have your ca configured you can associate it with an interface on that you would like to enable MACsec.
interface GigabitEthernet 1/50 macsec connectivity-association test macsec encryption enable macsec enable
That has to be identically configured on both switches that you would like to connect to each other with MACsec enabled interfaces.
VSP4k-1:1#sho macsec connectivity-association
================================================================================ MACSEC Connectivity Associations Info ================================================================================ Connectivity Connectivity Port Association Name Association Key Members -------------------------------------------------------------------------------- test 112233445566778899aabbccddeeff00 1/50
VSP4k-1:1#sho macsec status
================================================================================ MACSEC Port Status ================================================================================ MACSEC Encryption Replay Replay Encryption CA PortId Status Status Protect Protect W'dow Offset Name -------------------------------------------------------------------------------- 1/50 enabled enabled disabled -- none test
VSP4k-1:1#sho macsec statistics 1/50
================================================================================ MACSEC Port Statistics ================================================================================ TxUntagged TxTooLong RxUntagged RxNoTag PortId Packets Packets Packets Packets -------------------------------------------------------------------------------- 1/50 0 0 0 648
RxBadTag RxUnknown RxNoSCI RxOverrun PortId Packets SCIPackets Packets Packets -------------------------------------------------------------------------------- 1/50 0 0 0 0
Note you will need an extra license to get the MACsec feature.
Cheers





Dominik, Thanks again for another good article. My only complaint, is that you waited until the last line to let us know that this is available with an additional license. A good article none the less. Thanks, Sean
At the moment it is also the only feature that needs an extra license on the VSP4k. I would also like that it would be free available, but I have seen far more advanced licensing models at some vendors especially in the scurity space.
very nice article about macsec. ..